help desk




help desk




computer security concept, to prevent cross-site scripting and related attacks
CSP is implemented in Extenso in sed_site_config:
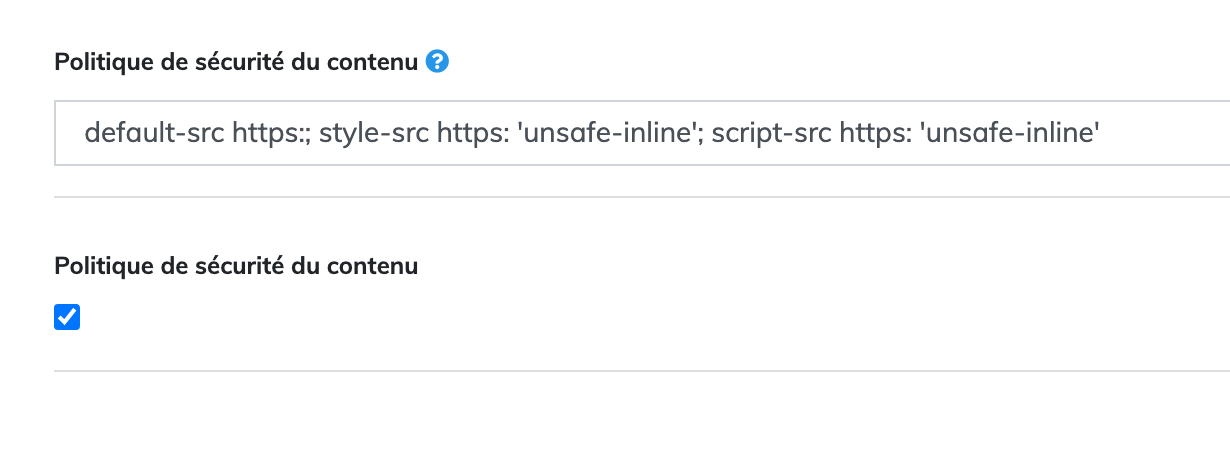
The default directive is rather unsafe. The page_v3 template implement this code:
{_{
// Implement Content-Security policy
site_config = sql(single:true, "select csp,csp_value from sed_site_config");
console("SITE=" .+ stringnify(site_config.rows));
if site_config.rows.csp_value ne "" && site_config.rows.csp eq "yes" then
}}
\{_{ nonce = uuid();
console("NONCE=".+nonce);
csp = resub(dq(()), "##\s*nonce\s*##",nonce,"g");
headers_out("Content-Security-Policy", csp);
console("CSP=" .+ csp);
}}
{_{
endif
}}
The variable nonce could be used to identify inline CSS and Javascript if you implement the following CSP directive:
default-src https:; style-src https: 'nonce-## nonce ##'; script-src https: 'nonce-## nonce ##'
In your inline CSS and Javascript you could use:
<style nonce="{_{ nonce }}">
h1 { color: blue;}
</style> <script nonce="{_{ nonce }}">
console.log('test');
</script>

Replied on: 2022-01-12 09:36:00